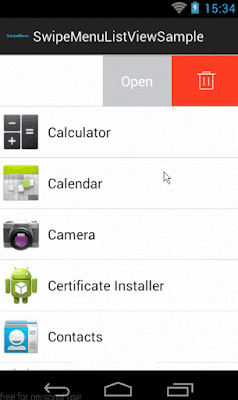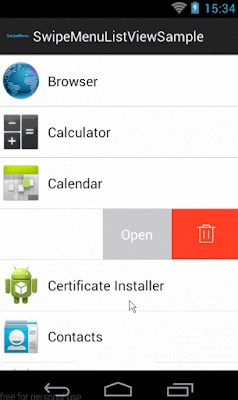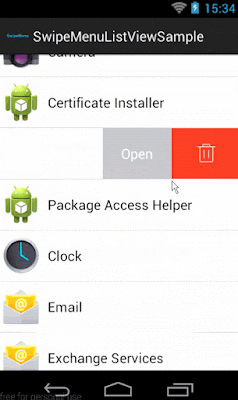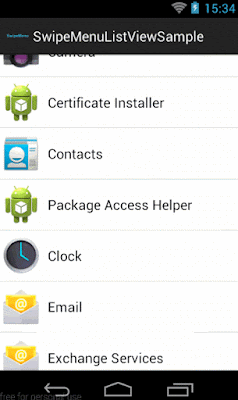
In this post, I will show how to implement SwipeMenuListView library. Basically, in iOS there is default option to manage actions while swipe the listview or will put as tableview cell. Similar, funtionality can be implemented in Android using SwipeMenuListView library.
Step 1 :- Add dependency.
Step 2 :- Add SwipeMenuListView in layout xml.
Step 3 :- Create a SwipeMenuCreator to add items.
Step 4 :- Add listener item click event.
Step 5 :- Decide swipe direction.
Refer the below link for complete sample code:-
Download Sample Code
MainActivity.java
activity_main.xml
Refer below link for more information and to find original project on github.
https://github.com/baoyongzhang/SwipeMenuListView
Step 1 :- Add dependency.
Step 2 :- Add SwipeMenuListView in layout xml.
Step 3 :- Create a SwipeMenuCreator to add items.
Step 4 :- Add listener item click event.
Step 5 :- Decide swipe direction.
Refer the below link for complete sample code:-
Download Sample Code
MainActivity.java
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 | package com.swipemenulistview_as; import android.app.Activity; import android.content.Context; import android.graphics.Color; import android.graphics.drawable.ColorDrawable; import android.os.Bundle; import android.view.LayoutInflater; import android.view.View; import android.view.ViewGroup; import android.widget.BaseAdapter; import android.widget.TextView; import android.widget.Toast; import java.util.ArrayList; import java.util.Arrays; import swipemenulistview.SwipeMenu; import swipemenulistview.SwipeMenuCreator; import swipemenulistview.SwipeMenuItem; import swipemenulistview.SwipeMenuListView; /** * This class is used for showing swipemenulistview. */ public class MainActivity extends Activity { private String[] arrData = { "Harshal Benake 0", "Harshal Benake 1", "Harshal Benake 2", "Harshal Benake 3", "Harshal Benake 4", "Harshal Benake 5", "Harshal Benake 6", "Harshal Benake 7", "Harshal Benake 8", "Harshal Benake 9", "Harshal Benake 10" }; @Override protected void onCreate(Bundle savedInstanceState) { super.onCreate(savedInstanceState); setContentView(R.layout.activity_main); SwipeMenuListView swipeMenuListView = (SwipeMenuListView) findViewById(R.id.listView); SwipeMenuCreator creator = new SwipeMenuCreator() { @Override public void create(SwipeMenu menu) { // create "item1" SwipeMenuItem item1 = new SwipeMenuItem(getApplicationContext()); // set item background item1.setBackground(new ColorDrawable(Color.parseColor("#FF9933"))); // set item width item1.setWidth(100); // set item title item1.setTitle("Item 1"); // set item title fontsize item1.setTitleSize(18); // set item title font color item1.setTitleColor(Color.WHITE); // set a icon // item1.setIcon(R.drawable.ic_launcher); // add to menu menu.addMenuItem(item1); // create "item2" SwipeMenuItem item2 = new SwipeMenuItem(getApplicationContext()); // set item background item2.setBackground(new ColorDrawable(Color.WHITE)); // set item width item2.setWidth(100); // set a icon item2.setIcon(R.drawable.ic_launcher); // add to menu menu.addMenuItem(item2); // create "item3" SwipeMenuItem item3 = new SwipeMenuItem(getApplicationContext()); // set item background item3.setBackground(new ColorDrawable(Color.parseColor("#138808"))); // set item width item3.setWidth(100); // set a icon //item3.setIcon(R.drawable.ic_launcher); // set item title item3.setTitle("Item 3"); // set item title fontsize item3.setTitleSize(18); // set item title font color item3.setTitleColor(Color.WHITE); // add to menu menu.addMenuItem(item3); } }; // set creator swipeMenuListView.setMenuCreator(creator); swipeMenuListView.setOnMenuItemClickListener(new SwipeMenuListView.OnMenuItemClickListener() { @Override public boolean onMenuItemClick(int position, SwipeMenu menu, int index) { switch (index) { case 0: Toast.makeText(MainActivity.this, "Item 1 pressed", Toast.LENGTH_SHORT).show(); break; case 1: Toast.makeText(MainActivity.this, "Item 2 pressed", Toast.LENGTH_SHORT).show(); break; case 2: Toast.makeText(MainActivity.this, "Item 3 pressed", Toast.LENGTH_SHORT).show(); break; } // false : close the menu; true : not close the menu return false; } }); // Right // swipeMenuListView.setSwipeDirection(SwipeMenuListView.DIRECTION_RIGHT); // Left swipeMenuListView.setSwipeDirection(SwipeMenuListView.DIRECTION_LEFT); swipeMenuListView.setOnSwipeListener(new SwipeMenuListView.OnSwipeListener() { @Override public void onSwipeStart(int position) { // swipe start System.out.println("setOnSwipeListener onSwipeStart"); } @Override public void onSwipeEnd(int position) { // swipe end System.out.println("setOnSwipeListener onSwipeEnd"); } }); ArrayList arrayList = new ArrayList<>(); arrayList.addAll(Arrays.asList(arrData)); CustomAdapter customAdapter=new CustomAdapter(arrayList); swipeMenuListView.setAdapter(customAdapter); } /** * Custom Adapter for listview. */ class CustomAdapter extends BaseAdapter { private ArrayList<String> mData = new ArrayList<String>(); private LayoutInflater mInflater; public CustomAdapter(ArrayList arrayList) { mInflater = (LayoutInflater) getSystemService(Context.LAYOUT_INFLATER_SERVICE); mData=arrayList; } @Override public int getCount() { return mData.size(); } @Override public String getItem(int position) { return mData.get(position); } @Override public long getItemId(int position) { return position; } @Override public View getView(int position, View convertView, ViewGroup parent) { ViewHolder holder = null; int type = getItemViewType(position); if (convertView == null) { holder = new ViewHolder(); convertView = mInflater.inflate(R.layout.row_item, null); holder.textView = (TextView) convertView.findViewById(R.id.textView); convertView.setTag(holder); } else { holder = (ViewHolder) convertView.getTag(); } holder.textView.setText(mData.get(position)); return convertView; } } public class ViewHolder { public TextView textView; } } |
activity_main.xml
1 2 3 4 5 6 7 8 9 10 | <RelativeLayout xmlns:android="http://schemas.android.com/apk/res/android" xmlns:tools="http://schemas.android.com/tools" android:layout_width="match_parent" android:layout_height="match_parent"> <swipemenulistview.SwipeMenuListView android:id="@+id/listView" android:layout_width="match_parent" android:layout_height="match_parent" /> </RelativeLayout> |
Refer below link for more information and to find original project on github.
https://github.com/baoyongzhang/SwipeMenuListView