ProRat is a Remote Administration Tool made by PRO Group. It was written in C programming language and its capable to work with all windows operating systems. It is made for remoting your own computers from other computers. It is a Microsoft Windows based backdoor trojan horse, more commonly known as a RAT (Remote Administration Tool). As with other trojan horses it uses a client and server. It opens a port on the computer which allows the client to perform numerous operations on the server (the machine being controlled).
Features of ProRAT:-
ProRat allows many malicious actions on the victim's machine. Some of its abilities include:
Logging keystrokes
Full control over files
Drive formatting
Open/close CD tray
Hide taskbar, desktop, and start button
Writing on-screen
Movement of cursor
Feed the cat
Take screenshots
View system information
View webcam
Download & run files
Password Protect your bound server from being used by anyone else
It also has a server creator which features that allow it to be undetected by antivirus and firewall software, and also allow it to stealthily run in the background.
How to remotely control computers using ProRAT: -
Features of ProRAT:-
ProRat allows many malicious actions on the victim's machine. Some of its abilities include:
Logging keystrokes
Full control over files
Drive formatting
Open/close CD tray
Hide taskbar, desktop, and start button
Writing on-screen
Movement of cursor
Feed the cat
Take screenshots
View system information
View webcam
Download & run files
Password Protect your bound server from being used by anyone else
It also has a server creator which features that allow it to be undetected by antivirus and firewall software, and also allow it to stealthily run in the background.
How to remotely control computers using ProRAT: -
- Download ProRat. Once it is downloaded right click on the folder and choose to extract it, antivirus will detect it as trojan but it is a false positive detection. Open up the program.
- Next create the actual Trojan file. Click on Create and choose Create ProRat Server.
- Next put in your IP address so the server could connect to you. If you don’t know your IP address click on the little arrow to have it filled in for you automatically. Next put in your e-mail so that when and if a victim gets infected it will send you a message.
- Click on the General Settings button to continue. Choose the server port the program will connect through, the password you will be asked to enter when the victim is infected and you wish to connect with them, and the victim name. You can see ProRat has the ability to disable the windows firewall and hide itself from being displayed in the task manager.
- Click on the Bind with File button to continue. Here you will have the option to bind the trojan server file with another file. Remember a trojan can only be executed if a human runs it. So by binding it with a legitimate file like a text document or a game, the chances of someone clicking it go up. Check the bind option and select a file to bind it to.
- Click on the Server Extensions button to continue. Choose what kind of server file togenerate. Mostly exe’s looks suspicious so it would be smart to change it. Click on Server Icon to continue. Here you will choose an icon for your server file to have. The icons help mask what the file actually is.
- Finally click on Create Server to, you guessed it, create the server file.
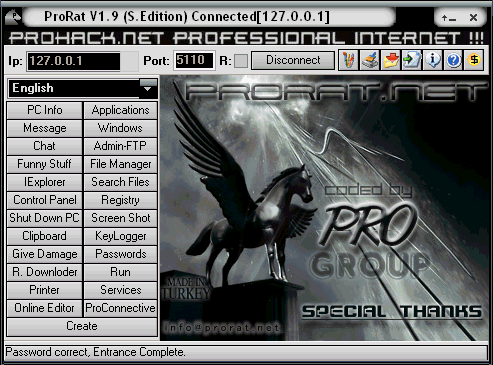
- Once the trojan runs on victims computer the attacker would then get a message telling him that victim was infected. He would then connect to computer by typing in my IP address, port and clicking Connect. He will be asked for the password that he made when he created the server. Once he types it in, he will be connected to victims computer and have full controlover it.
- First thing you need do is reboot the computer in Safe Mode with Networking to avoid Trojan Prorat from loading at start-up.
- Remove all media such as floppy drive, cd, dvd, and USB devices. Then, restart the computer.
- Once Windows is running under Safe Mode with Networking, open your antivirus program and download the most recent update. This method ensures that your antivirus program can detect even newer variants of Trojan Prorat.
- Once updating is finished, run a full system scan. After the scan, delete all infected items. If unable to clean or delete, better place the threat in quarantine.
- In future, try not to click or open unknown files or links.



No comments:
Post a Comment